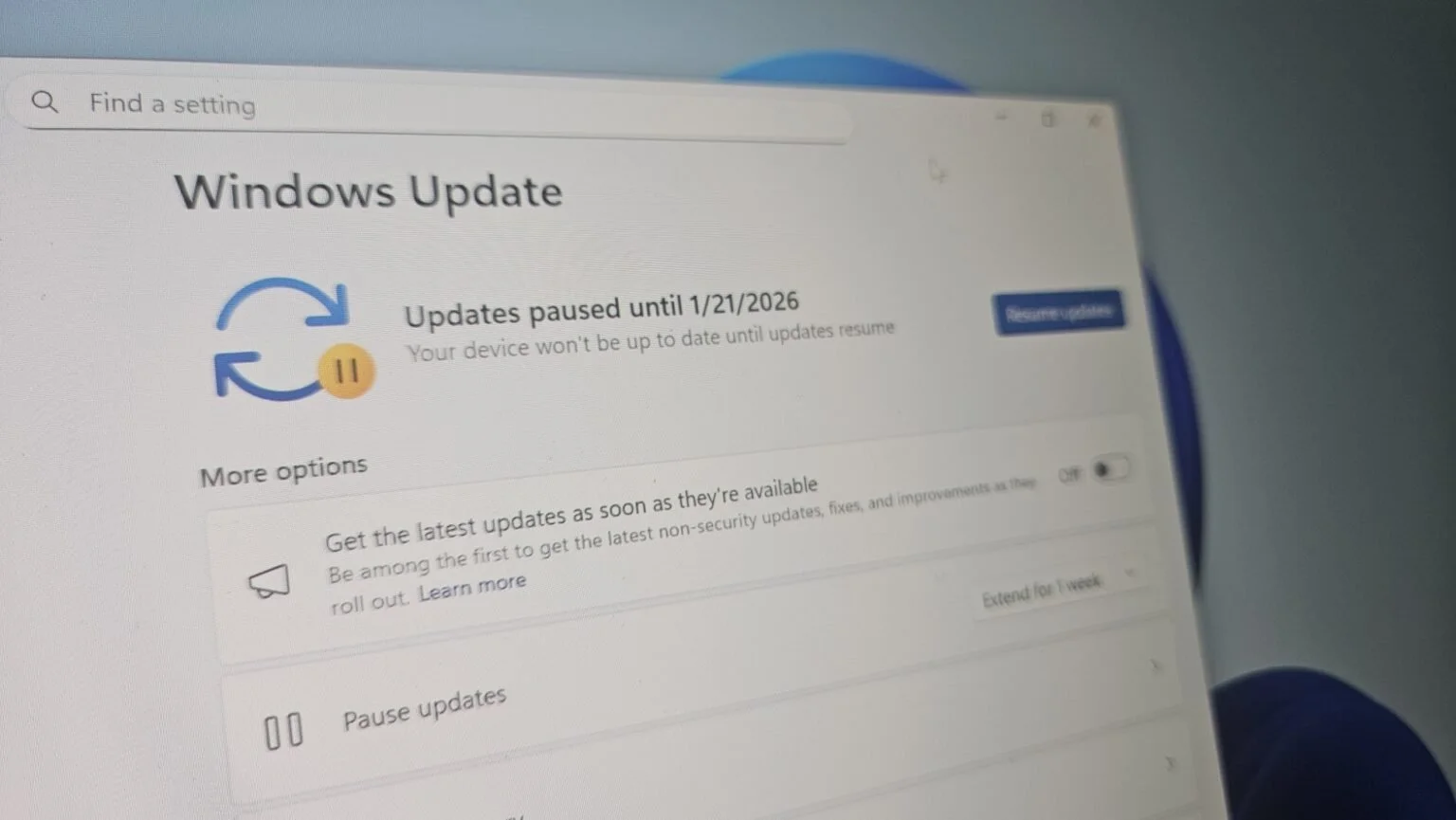
Released March 7, 2024
Admin Framework
Available for: macOS Monterey
Impact: An app may be able to elevate privileges
Description: A logic issue was addressed with improved checks.
CVE-2024-23276: Kirin (@Pwnrin)
Airport
Available for: macOS Monterey
Impact: An app may be able to read sensitive location information
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2024-23227: Brian McNulty
AppleMobileFileIntegrity
Available for: macOS Monterey
Impact: An app may be able to modify protected parts of the file system
Description: A downgrade issue affecting Intel-based Mac computers was addressed with additional code-signing restrictions.
CVE-2024-23269: Mickey Jin (@patch1t)
ColorSync
Available for: macOS Monterey
Impact: Processing a file may lead to unexpected app termination or arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2024-23247: m4yfly with TianGong Team of Legendsec at Qi'anxin Group
CoreCrypto
Available for: macOS Monterey
Impact: An attacker may be able to decrypt legacy RSA PKCS#1 v1.5 ciphertexts without having the private key
Description: A timing side-channel issue was addressed with improvements to constant-time computation in cryptographic functions.
CVE-2024-23218: Clemens Lang
Dock
Available for: macOS Monterey
Impact: An app from a standard user account may be able to escalate privilege after admin user login
Description: A logic issue was addressed with improved restrictions.
CVE-2024-23244: Csaba Fitzl (@theevilbit) of OffSec
Image Processing
Available for: macOS Monterey
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: The issue was addressed with improved memory handling.
CVE-2024-23270: an anonymous researcher
ImageIO
Available for: macOS Monterey
Impact: Processing an image may lead to arbitrary code execution
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2024-23286: Dohyun Lee (@l33d0hyun)
ImageIO
Available for: macOS Monterey
Impact: Processing an image may result in disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2024-23257: Junsung Lee working with Trend Micro Zero Day Initiative
Intel Graphics Driver
Available for: macOS Monterey
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2024-23234: Murray Mike
Kerberos v5 PAM module
Available for: macOS Monterey
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2024-23266: Pedro Tôrres (@t0rr3sp3dr0)
Kernel
Available for: macOS Monterey
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: A memory corruption vulnerability was addressed with improved locking.
CVE-2024-23265: Xinru Chi of Pangu Lab
Kernel
Available for: macOS Monterey
Impact: An attacker with arbitrary kernel read and write capability may be able to bypass kernel memory protections. Apple is aware of a report that this issue may have been exploited.
Description: A memory corruption issue was addressed with improved validation.
CVE-2024-23225
libxpc
Available for: macOS Monterey
Impact: An app may be able to cause a denial-of-service
Description: A permissions issue was addressed with additional restrictions.
CVE-2024-23201: Koh M. Nakagawa of FFRI Security, Inc. and an anonymous researcher
MediaRemote
Available for: macOS Monterey
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2023-28826: Meng Zhang (鲸落) of NorthSea
Metal
Available for: macOS Monterey
Impact: An application may be able to read restricted memory
Description: A validation issue was addressed with improved input sanitization.
CVE-2024-23264: Meysam Firouzi @R00tkitsmm working with Trend Micro Zero Day Initiative
Notes
Available for: macOS Monterey
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2024-23283
PackageKit
Available for: macOS Monterey
Impact: An app may be able to elevate privileges
Description: An injection issue was addressed with improved input validation.
CVE-2024-23274: Bohdan Stasiuk (@Bohdan_Stasiuk)
CVE-2024-23268: Mickey Jin (@patch1t), and Pedro Tôrres (@t0rr3sp3dr0)
PackageKit
Available for: macOS Monterey
Impact: An app may be able to access protected user data
Description: A race condition was addressed with additional validation.
CVE-2024-23275: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Monterey
Impact: An app may be able to bypass certain Privacy preferences
Description: The issue was addressed with improved checks.
CVE-2024-23267: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Monterey
Impact: An app may be able to overwrite arbitrary files
Description: A path handling issue was addressed with improved validation.
CVE-2024-23216: Pedro Tôrres (@t0rr3sp3dr0)
SharedFileList
Available for: macOS Monterey
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved file handling.
CVE-2024-23230: Mickey Jin (@patch1t)
Shortcuts
Available for: macOS Monterey
Impact: A shortcut may be able to use sensitive data with certain actions without prompting the user
Description: The issue was addressed with additional permissions checks.
CVE-2024-23204: Jubaer Alnazi (@h33tjubaer)
Shortcuts
Available for: macOS Monterey
Impact: Third-party shortcuts may use a legacy action from Automator to send events to apps without user consent
Description: This issue was addressed by adding an additional prompt for user consent.
CVE-2024-23245: an anonymous researcher
Storage Services
Available for: macOS Monterey
Impact: A user may gain access to protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2024-23272: Mickey Jin (@patch1t)
Information about products not manufactured by Apple, or independent websites not controlled or tested by Apple, is provided without recommendation or endorsement. Apple assumes no responsibility with regard to the selection, performance, or use of third-party websites or products. Apple makes no representations regarding third-party website accuracy or reliability. Contact the vendor for additional information.
Published Date: March 07, 2024